| From | Miriam Bastian, FSF <[email protected]> |
| Subject | We have nothing to hide, only everything to protect |
| Date | June 21, 2023 12:39 AM |
Links have been removed from this email. Learn more in the FAQ.
Links have been removed from this email. Learn more in the FAQ.
*Please consider adding <[email protected]> to your address book, which
will ensure that our messages reach you and not your spam box.*
*Read and share online: <[link removed]>*
Dear Free Software Supporter,
"I have nothing to hide." That's what most people say when I start a
conversation about privacy. Have you ever wondered why you should use
software that protects your privacy and the privacy of the people you
communicate with? To understand this better, I recommend watching the
first talk in our LibrePlanet 2023 [lightning talk][1] series. In her
five minute talk, the speaker will convince you that you are worthy of
all the privacy you want and need. For people who claim that they have
nothing to hide, she has a persuasive reply: "I have nothing to hide,
only everything to protect."
[1]: [link removed]
If you don't use free software for the sake of your own privacy, then
use it to protect your loved ones; if you don't value yourself enough
to make sure that information that's yours -- and only yours -- stays
with you, then at least honor the privacy of the most vulnerable
people in our society. History shows that even societies that are
considered to be free have areas in which they struggle to exercise
equal treatment and fail to guarantee human rights for everyone who
lives within them. In the above-mentioned lightning talk, the speaker
cites the example of the [Underground Railroad][2], a network of
secret routes and safe houses that helped enslaved African Americans
in the 19th century escape from slavery. The Underground Railroad
would not have been possible without privacy!
[2]: [link removed]
At a time when ongoing legislation all over the world is threatening
end-to-end encryption and developers of large language models
blatantly [violate privacy laws][3] to get training data for their
systems, we will be publishing a series of articles to highlight the
importance of privacy. In our upcoming articles, you will be
introduced to people who use privacy-protecting free software and
learn what you can do to counter the dangers resulting from the
ongoing legislative processes. While waiting for these articles, you
can read our [previous articles on privacy][4] and strengthen
end-to-end encryption by using it.
[3]: [link removed]
[4]: [link removed]
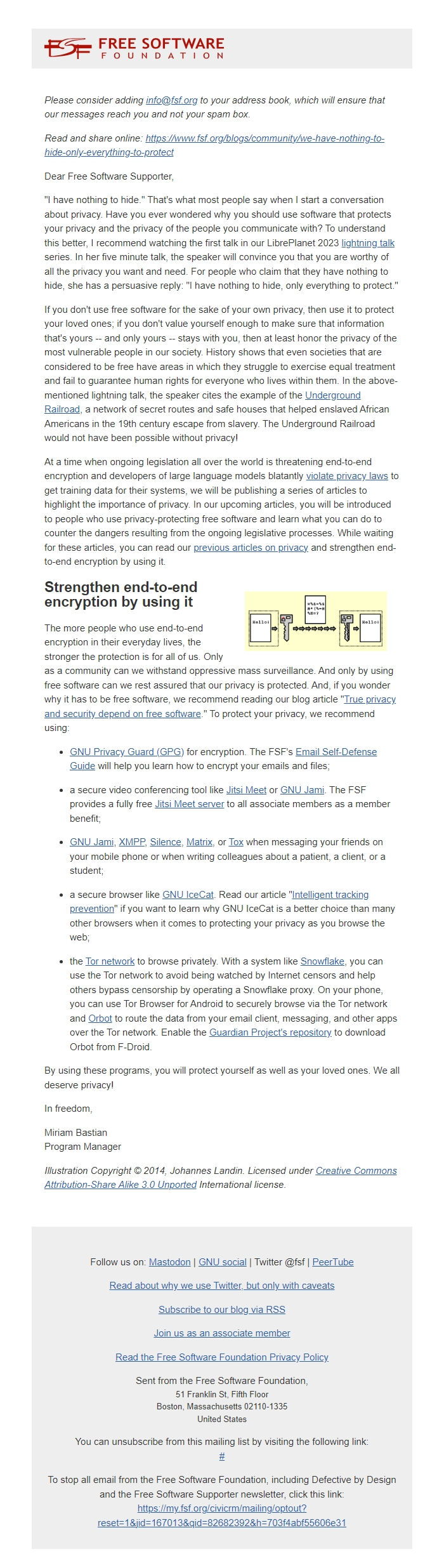
## Strengthen end-to-end encryption by using it
The more people who use end-to-end encryption in their everyday lives,
the stronger the protection is for all of us. Only as a community can
we withstand oppressive mass surveillance. And only by using free
software can we rest assured that our privacy is protected. And, if
you wonder why it has to be free software, we recommend reading our
blog article "[True privacy and security depend on free software][5]."
To protect your privacy, we recommend using:
* [GNU Privacy Guard (GPG)][6] for encryption. The FSF's [Email
Self-Defense Guide][7] will help you learn how to encrypt your
emails and files;
* a secure video conferencing tool like [Jitsi Meet][8] or [GNU
Jami][9]. The FSF provides a fully free [Jitsi Meet server][10] to
all associate members as a member benefit;
* [GNU Jami][9], [XMPP][11], [Silence][12], [Matrix][13], or [Tox][14]
when messaging your friends on your mobile phone or when writing
colleagues about a patient, a client, or a student;
* a secure browser like [GNU IceCat][15]. Read our article
"[Intelligent tracking prevention][16]" if you want to learn why GNU
IceCat is a better choice than many other browsers when it comes to
protecting your privacy as you browse the web;
* the [Tor network][17] to browse privately. With a system like
[Snowflake][18], you can use the Tor network to avoid being watched
by Internet censors and help others bypass censorship by operating a
Snowflake proxy. On your phone, you can use Tor Browser for Android
to securely browse via the Tor network and [Orbot][19] to route the
data from your email client, messaging, and other apps over the Tor
network. Enable the [Guardian Project's repository][20] to download
Orbot from F-Droid.
By using these programs, you will protect yourself as well as your
loved ones. We all deserve privacy!
[5]: [link removed]
[6]: [link removed]
[7]: [link removed]
[8]: [link removed]
[9]: [link removed]
[10]: [link removed]
[11]: [link removed]
[12]: [link removed]
[13]: [link removed]
[14]: [link removed]
[15]: [link removed]
[16]: [link removed]
[17]: [link removed]
[18]: [link removed]
[19]: [link removed]
[20]: [link removed]
In freedom,
Miriam Bastian
Program Manager
--
* Follow us on Mastodon at <[link removed]>, GNU social at
<[link removed]>, PeerTube at <[link removed]>, and on Twitter at @fsf.
* Read about why we use Twitter, but only with caveats: <[link removed]>
* Subscribe to our RSS feeds: <[link removed]>
* Join us as an associate member: <[link removed]>
* Read our Privacy Policy: <[link removed]>
Sent from the Free Software Foundation,
51 Franklin St, Fifth Floor
Boston, Massachusetts 02110-1335
United States
You can unsubscribe from this mailing list by visiting
[link removed].
To stop all email from the Free Software Foundation, including Defective by Design,
and the Free Software Supporter newsletter, visit
[link removed].
will ensure that our messages reach you and not your spam box.*
*Read and share online: <[link removed]>*
Dear Free Software Supporter,
"I have nothing to hide." That's what most people say when I start a
conversation about privacy. Have you ever wondered why you should use
software that protects your privacy and the privacy of the people you
communicate with? To understand this better, I recommend watching the
first talk in our LibrePlanet 2023 [lightning talk][1] series. In her
five minute talk, the speaker will convince you that you are worthy of
all the privacy you want and need. For people who claim that they have
nothing to hide, she has a persuasive reply: "I have nothing to hide,
only everything to protect."
[1]: [link removed]
If you don't use free software for the sake of your own privacy, then
use it to protect your loved ones; if you don't value yourself enough
to make sure that information that's yours -- and only yours -- stays
with you, then at least honor the privacy of the most vulnerable
people in our society. History shows that even societies that are
considered to be free have areas in which they struggle to exercise
equal treatment and fail to guarantee human rights for everyone who
lives within them. In the above-mentioned lightning talk, the speaker
cites the example of the [Underground Railroad][2], a network of
secret routes and safe houses that helped enslaved African Americans
in the 19th century escape from slavery. The Underground Railroad
would not have been possible without privacy!
[2]: [link removed]
At a time when ongoing legislation all over the world is threatening
end-to-end encryption and developers of large language models
blatantly [violate privacy laws][3] to get training data for their
systems, we will be publishing a series of articles to highlight the
importance of privacy. In our upcoming articles, you will be
introduced to people who use privacy-protecting free software and
learn what you can do to counter the dangers resulting from the
ongoing legislative processes. While waiting for these articles, you
can read our [previous articles on privacy][4] and strengthen
end-to-end encryption by using it.
[3]: [link removed]
[4]: [link removed]
## Strengthen end-to-end encryption by using it
The more people who use end-to-end encryption in their everyday lives,
the stronger the protection is for all of us. Only as a community can
we withstand oppressive mass surveillance. And only by using free
software can we rest assured that our privacy is protected. And, if
you wonder why it has to be free software, we recommend reading our
blog article "[True privacy and security depend on free software][5]."
To protect your privacy, we recommend using:
* [GNU Privacy Guard (GPG)][6] for encryption. The FSF's [Email
Self-Defense Guide][7] will help you learn how to encrypt your
emails and files;
* a secure video conferencing tool like [Jitsi Meet][8] or [GNU
Jami][9]. The FSF provides a fully free [Jitsi Meet server][10] to
all associate members as a member benefit;
* [GNU Jami][9], [XMPP][11], [Silence][12], [Matrix][13], or [Tox][14]
when messaging your friends on your mobile phone or when writing
colleagues about a patient, a client, or a student;
* a secure browser like [GNU IceCat][15]. Read our article
"[Intelligent tracking prevention][16]" if you want to learn why GNU
IceCat is a better choice than many other browsers when it comes to
protecting your privacy as you browse the web;
* the [Tor network][17] to browse privately. With a system like
[Snowflake][18], you can use the Tor network to avoid being watched
by Internet censors and help others bypass censorship by operating a
Snowflake proxy. On your phone, you can use Tor Browser for Android
to securely browse via the Tor network and [Orbot][19] to route the
data from your email client, messaging, and other apps over the Tor
network. Enable the [Guardian Project's repository][20] to download
Orbot from F-Droid.
By using these programs, you will protect yourself as well as your
loved ones. We all deserve privacy!
[5]: [link removed]
[6]: [link removed]
[7]: [link removed]
[8]: [link removed]
[9]: [link removed]
[10]: [link removed]
[11]: [link removed]
[12]: [link removed]
[13]: [link removed]
[14]: [link removed]
[15]: [link removed]
[16]: [link removed]
[17]: [link removed]
[18]: [link removed]
[19]: [link removed]
[20]: [link removed]
In freedom,
Miriam Bastian
Program Manager
--
* Follow us on Mastodon at <[link removed]>, GNU social at
<[link removed]>, PeerTube at <[link removed]>, and on Twitter at @fsf.
* Read about why we use Twitter, but only with caveats: <[link removed]>
* Subscribe to our RSS feeds: <[link removed]>
* Join us as an associate member: <[link removed]>
* Read our Privacy Policy: <[link removed]>
Sent from the Free Software Foundation,
51 Franklin St, Fifth Floor
Boston, Massachusetts 02110-1335
United States
You can unsubscribe from this mailing list by visiting
[link removed].
To stop all email from the Free Software Foundation, including Defective by Design,
and the Free Software Supporter newsletter, visit
[link removed].
Message Analysis
- Sender: Free Software Foundation
- Political Party: n/a
- Country: United States
- State/Locality: n/a
- Office: n/a
-
Email Providers:
- CiviCRM
